Azure Administrator Associate(AZ-104)
Prerequiresites
Cloud Shell
- Is temporary and requires a new or existing Azure Files share to be mounted.
- Offers an integrated graphical text editor based on the open-source Monaco Editor.
- Authenticates automatically for instant access to your resources.
- Runs on a temporary host provided on a per-session, per-user basis.
- Times out after 20 minutes without interactive activity.
- Requires a
resource group,storage account, andAzure File share. - Uses the same Azure file share for both Bash and PowerShell.
- Is assigned to one machine per user account.
- Persists $HOME using a 5-GB image held in your file share.
- Permissions are set as a regular Linux user in Bash.
Azure CLI
Tip
use az find <target> to find the particular command
Azure Powershell
- Sample code for Azure PowerShell documentation
- 🔗Which PowerShell Commands I should know for AZ-104 Certification?
Azure Resource Manager

- resource: A manageable item that is available through Azure.
- resource group: A container that holds related resources for an Azure solution.
- resource provider:
- A service that supplies the resources you can deploy and manage through Resource Manager.
- Each resource provider offers operations for working with the resources that are deployed.
- Some common resource providers are:
- Microsoft.Compute - supplies the virtual machine resource
- Microsoft.Storage - supplies the storage account resource
- Microsoft.Web - supplies resources related to web apps.
- The name of a resource type is in the format:
{resource-provider}/{resource-type}. - Resource providers for Azure services
- template: A JavaScript Object Notation (JSON) file that defines one or more resources to deploy to a resource group. It also defines the dependencies between the deployed resources.
- declarative syntax: Syntax that lets you state "Here is what I intend to create" without having to write the sequence of programming commands to create it.
Resource Group
- All the resources in your group should share the same lifecycle.
- Each resource can only exist in one resource group
- You can add or remove a resource to a resource group at any time.
- You can move a resource from one resource group to another group.
- A resource group can contain resources that reside in different regions.
- A resource group can be used to scope access control for administrative actions.
- A resource can interact with resources in other resource groups.
Tip
The resource group stores metadata about the resources. Therefore, when you specify a location for the resource group, you're specifying where that metadata is stored.
Azure Resource Manager locks
- Read-Only locks: prevent any changes to the resource.
- Delete locks: prevent deletion.
Note
Only the Owner and User Access Administrator roles can create or delete management locks.
Reorganize Resources
- When moving resources, both the source group and the target group are locked during the operation.
- Write and delete operations are blocked on the resource groups until the move completes.
- This lock means you can't add, update, or delete resources in the resource groups.
- Locks don't mean the resources aren't available.
Azure Resource Manager templates
An Azure Resource Manager template is a JSON file that defines the infrastructure and configuration for the deployment.
Tip
The template uses a declarative syntax. The declarative syntax is a way of building the structure and elements that outline what resources will look like without describing its control flow. Declarative syntax is different than imperative syntax, which uses commands for the computer to perform. Imperative scripting focuses on specifying each step in deploying the resources.
Infrastructure as code
Infrastructure as code enables you to describe, through code, the infrastructure that you need for your application.
The advantages to infrastructure as code are:
- Consistent configurations
- Improved scalability
- Faster deployments
- Better traceability
schema
{
"$schema": "http://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
"contentVersion": "",
"parameters": {},
"variables": {},
"functions": [],
"resources": [],
"outputs": {}
}
$schema:- Required: Yes
- Location of the JSON schema file that describes the version of the template language.
contentVersion- Required: Yes
- You can provide any value for this element. Use this value to document significant changes in your template.
parameters- Required: No
- Values that are provided when deployment is executed to customize resource deployment.
- These values can be provided by a parameter file, by command-line parameters, or in the Azure portal.
variables- Required: No
- Values that are used as JSON fragments in the template to simplify template language expressions.
functions- Required: No
- User-defined functions that are available within the template.
- User-defined functions can simplify your template when complicated expressions are used repeatedly in your template.
resources- Required: Yes
- Resource types that are deployed or updated in a resource group.
outputs- Required: No
- Values that are returned after deployment.
Note
The available properties for a parameter are:
"parameters": {
"<parameter-name>": {
"type": "<type-of-parameter-value>",
"defaultValue": "<default-value-of-parameter>",
"allowedValues": [
"<array-of-allowed-values>"
],
"minValue": <minimum-value-for-int>,
"maxValue": <maximum-value-for-int>,
"minLength": <minimum-length-for-string-or-array>,
"maxLength": <maximum-length-for-string-or-array-parameters>,
"metadata": {
"description": "<description-of-the-parameter>"
}
}
}
The allowed types of parameters are:
- string
- secureString - for all passwords and secrets
- integers
- boolean
- object
- secureObject - for sensitive data
- array
QuickStart Templates
- The
README.mdfile provides an overview of what the template does. - The
azuredeploy.jsonfile defines the resources that will be deployed. - The
azuredeploy.parameters.jsonfile provides the values the template needs.
Cloud Pricing Models
Always FREE
- Virtual Network
- Azure Policy
- Azure Active Directory
- Azure Migrate
- Azure Open Datasets
- Azure Lighthouse
- Azure Private Link
- Azure Data Catalog
- Azure Service Fabric
Pay: Time
- Charge based on time you use a particular service
- Other imp parameters like performance tiers and other configurations
- Examples:
- Virtual Machine
- App Services
- SQL Database
- Load Balancer
Pay: GB
- Database Storage
- Storage Service
- Network traffic (between regions)
Pay: Operations
- Charges based on number of operation
- Example: Cost per million operation
- Storage services (read, write or delete operations)
- Cosmos DB
Pay: Execution
- Serverless offerings
- Charges only when you use, per execution
- Examples:
- Azure Function
- Serverless Database
- Logic Apps
Pay: Other Metrics
- Example: Azure Active Directory Premium tier
- Charge based on number of user licenses
Ways to Optimize Cost
- Shut down unused resources
- Right-size underused resources
- RIs for consistent workloads
- Choose the right Azure compute service
- Setup budgets
- Configure autoscaling
- Azure Hybrid Benefit
- EA - Enterprise Agreement
- Price Match with AWS
Organizing structure for resources
Resource Groups
- Resources: are anything you create in an Azure subscription like VMs, Azure Application Gateway instances, and Azure Cosmos DB instances.
- Resource group is a logical container which help manage and organize your Azure resources.
- For example similar usage, type, or location
- Each resource can exist in only one resource group.
- You can move a resource from one resource group to another group.
- Resource groups can't be nested.
- The resources in a resource group can be located in different regions than the resource group.
- Resource group created at location – to store metadata.
- A resource group can be used to scope access control for administrative actions. To manage a resource group, you can assign Azure Policies, Azure roles, or resource locks.
- You can apply locks to a resource group or subscription to prevent deletion or make contained resources read-only. You can also apply locks directly to a resource.
- You can apply tags to a resource group. The resources in the resource group don't inherit those tags.
- Life cycle: When you delete a resource group, all resources in the resource group are also deleted.
- To create a resource group, you can use the portal, PowerShell, Azure CLI, or an ARM template.
Subscription
- Using Azure requires an Azure subscription.
- An Azure subscription is a logical unit of Azure services that links to an Azure account. It also allows you to provision resources.
- A subscription provides you with authenticated and authorized access to Azure products and services.
- Azure generates separate billing reports and invoices for each subscription
- Two types of subscription boundaries
- Billing boundary
- Access control boundary
- You can create separate subscription based on:
- Environment: development and testing, security, or to isolate data for compliance reasons
- Organizational structures: IT, HR, Admin and so on
- Billing: manage and track costs based on your needs, for example – Production, Test and Dev
- Different types of Subscription:
- FREE: An email address and a credit card are required to sign up for a free trial subscription that provides $200 credit for the first 30 days and 12 months of restricted access.
- Pay-Per-Use: Charges monthly based on Cloud resource use.
- Enterprise: A single Enterprise agreement is established for large subscription purchases, including savings for new licenses and Software Assurance.
- Student: This membership includes $100 for 12 months and may be activated without a credit card.
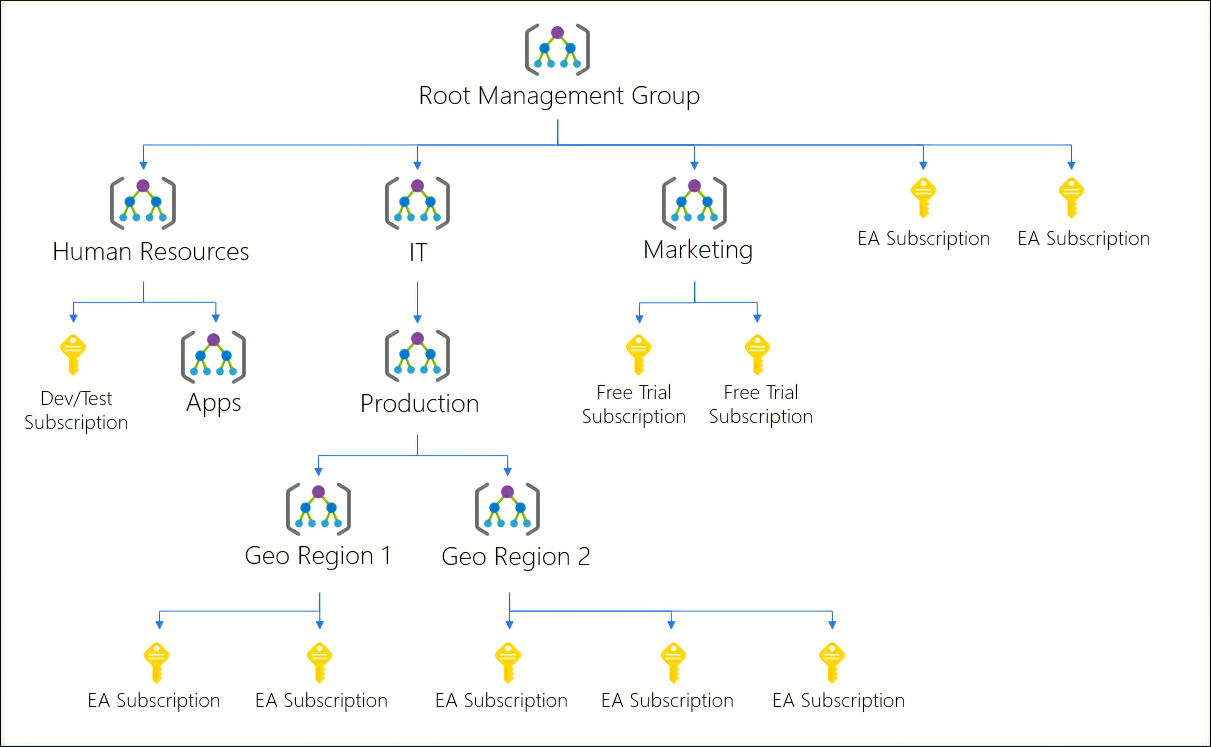
Management Groups
- Management groups let you organize multiple subscriptions as a single management entity to facilitate easier management.
- You can create managements groups in a hierarchical structure with the top level of the hierarchy at the tenant level and containing all subscriptions in that tenant.
- Any conditions applied to a management group apply to all subscriptions contained in that management group object.
- Each management group and subscription can support only one parent.
- Each management group can have many children.
- The root management group can't be moved or deleted, unlike other management groups.
Move Resources
- App Service
- You need to delete the Secure Sockets Layer(SSL) certificate from each App Service before moving it to the new resource group
- You cannot move an App Service with an SSL certificate configured
- You need to delete the certificate first, move the App Service, and then upload the certificate again
- Load Balancer
- You cannot move the Load Balancer within the same subscription
- A Standard Load Balancer cannot be moved either within the same subscription or between subscriptions
- VNet
- When you want to move a VNet with a peer configured, you need to disable it before moving the VNet
- When you move a VNet, you need to move all of its dependent resources
- You can only move the VNet within the same subscription
Manage identities and governance in Azure
Azure Active Directory
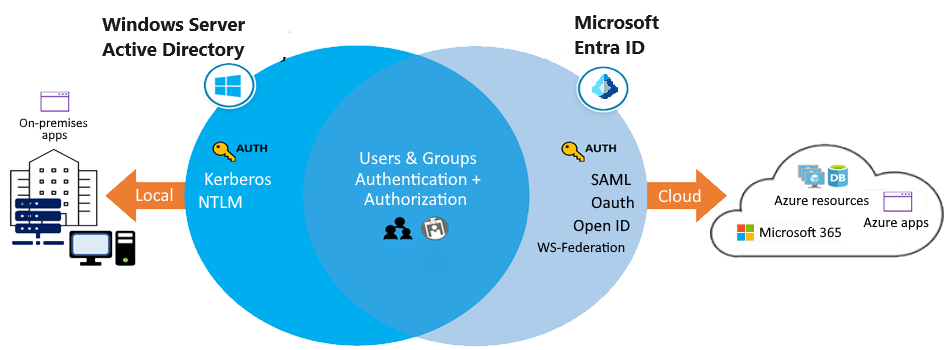
Azure Active Directory (Azure AD) is Microsoft's multi-tenant cloud-based directory and identity management service.
Info
Azure AD is primarily an identity solution. It's designed for internet-based applications by using HTTP and HTTPS communications.
AD VS AAD
- Communication – AD uses LDAP and AAD uses REST API
- Authentication – Cloud based protocols for AD/ AAD uses Kerberos and NTLM
- Access Setup – AD uses Admin/data owners and AAD organizes users into groups
- Network Organization – AD uses Forest/Domain/Tree/Organizational Unit (OU) whereas AAD uses users and groups
- Desktops – AD uses GPO (group policy object) and AAD can use Microsoft intune to join desktops
Azure AD Features
- Single sign-on(SSO) access
- Azure AD provides secure single sign-on (SSO) to web apps on the cloud and to on-premises apps.
- Users can sign in with the same set of credentials to access all their apps.
- Ubiquitous device support
- Azure AD works with iOS, macOS, Android, and Windows devices, and offers a common experience across the devices.
- Users can launch apps from a personalized web-based access panel, mobile app, Microsoft 365, or custom company portals by using their existing work credentials.
- Secure remote access
- Azure AD enables secure remote access for on-premises web apps.
- Secure access can include multifactor authentication (MFA), conditional access policies, and group-based access management.
- Users can access on-premises web apps from everywhere, including from the same portal.
- Cloud extensibility
- Azure AD can extend to the cloud to help you manage a consistent set of users, groups, passwords, and devices across environments.
- Sensitive data protection
- Azure AD offers unique identity protection capabilities to secure your sensitive data and apps.
- Admins can monitor for suspicious sign-in activity and potential vulnerabilities in a consolidated view of users and resources in the directory.
- Self-service support
- Azure AD lets you delegate tasks to company employees that might otherwise be completed by admins with higher access privileges.
- Providing self-service app access and password management through verification steps can reduce helpdesk calls and enhance security.
Azure AD Concepts
- Identity
- An identity is an object that can be authenticated.
- The identity can be a user with a username and password.
- Identities can also be applications or other servers that require authentication by using secret keys or certificates.
- Azure AD is the underlying product that provides the identity service.
- Account
- An account is an identity that has data associated with it.
- To have an account, you must first have a valid identity.
- You can't have an account without an identity.
- Azure AD Account
- An Azure AD account is an identity that's created through Azure AD or another Microsoft cloud service, such as Microsoft 365.
- Identities are stored in Azure AD and are accessible to your organization's cloud service subscriptions.
- The Azure AD account is also called a work or school account.
- Azure Tenant
- An Azure tenant is a single dedicated and trusted instance of Azure AD.
- Each tenant (also called a directory) represents a single organization.
- When your organization signs up for a Microsoft cloud service subscription, a new tenant is automatically created.
- Because each tenant is a dedicated and trusted instance of Azure AD, you can create multiple tenants or instances.
- Azure Subscription
- An Azure subscription is used to pay for Azure cloud services.
- A subscription is linked to a credit card.
- Each subscription is joined to a single tenant.
- You can have multiple subscriptions.
Azure AD Editions
- Free
- included with an Azure subscription
- provides user and group management, on-premises directory synchronization, and basic reports
- Microsoft 365 Apps
- included with Microsoft 365
- provides Identity and Access Management for Microsoft 365 apps
- the extra support includes branding, MFA, group access management, and self-service password reset for cloud users
- Premium P1
- lets your hybrid users access both on-premises and cloud resources
- supports advanced administration like dynamic groups, self-service group management, and cloud write-back capabilities
- the extra features in P1 allow self-service password reset for
on-premisesusers.
- Premium P2
- offers Azure AD Identity Protection to help provide risk-based Conditional Access to your apps and critical company data
- Privileged Identity Management is included to help discover, restrict, and monitor administrators and their access to resources, and to provide just-in-time access when needed.
Conditional Access
- Azure Active Directory uses Conditional Access to grant (or deny) resource access based on identity signals.
- Who the user is (Administrator or normal user?)
- Where the user is (usual or unexpected location?)
- What device the user is requesting access from (is this a new device?)
- Based on signals AAD can decide to allow, deny, or require MFA access.
- Multi-authentication only if sign-in signals are unusual (like unexpected location)
- Need an Azure AD Premium P1 or P2 license
Single sign-on(SSO)
- Problem statement - Why we need it?
- Users had to create individual identity and password for each application
- Difficult to remember credentials, and it’s unsecure
- When a user leaves an organization, finding all those identities and disabling them can be difficult.
- Single sign-on allows users to sign in once and access multiple resources and applications from multiple providers.
- With SSO, you need to remember only one ID and one password.
- As users change roles or leave an organization, access is tied to a single identity and so it is easy to manage.
Azure AD Device Settings
- Azure AD registration
- User-owned devices (BYOD)
- Local user account to login in to device, corporate account to access resources
- Limited management
- Windows 10 or newer, iOS, Android, and macOS
- Example: A user in your organization wants to access your benefits enrollment tool from their home PC.
- Azure AD join
- Corporate-owned devices
- Corporate user account
- Full Intune management
- Windows 11 and Windows 10 devices, Windows Server 2019 Virtual Machines running in Azure
- Example: workers who work from home or are in remote branch offices with limited on-premises infrastructure.
- Hybrid Azure AD join
- Suitable for hybrid organizations with existing on-premises AD infrastructure
- Joined to on-premises AD and Azure AD requiring organizational account to sign in to the device
- Gives you all the benefits of being cloud enabled, with still having full access to your on-prem infrastructure.
SSPR
SSPR: self-service password reset
- SSPR is supported for all users, including cloud-only users.
- You can configure password writeback to update on-premises passwords.
- For cloud-only users, passwords are stored in Azure AD.
- You can configure SSPR registration by group or for all domain users.
- You cannot configure SSPR registration by user.
Configure User and Group Account
User Account Types
- Cloud identity
- A user account with a cloud identity is defined only in Azure AD.
- This type of user account includes administrator accounts and users who are managed as part of your organization.
- A cloud identity can be for user accounts defined in your Azure AD organization, and also for user accounts defined in an external Azure AD instance.
- When a cloud identity is removed from the primary directory, the user account is deleted.
- Directory-synchronized identity
- User accounts that have a directory-synchronized identity are defined in an on-premises Active Directory.
- A synchronization activity occurs via Azure AD Connect to bring these user accounts in to Azure.
- The source for these accounts is Windows Server Active Directory.
- Guest user
- Guest user accounts are defined outside Azure.
- Examples include user accounts from other cloud providers, and Microsoft accounts like an Xbox LIVE account.
- The source for guest user accounts is Invited user.
- Guest user accounts are useful when external vendors or contractors need access to your Azure resources.
Group Account Types
- Security groups: manage member and computer access to shared resources for a group of users
- Microsoft 365 groups: provide collaboration opportunities - Group members have access to a shared mailbox, calendar, files, SharePoint site, and more.
Configure Subscriptions
An Azure subscription is a logical unit of Azure services that's linked to an Azure account.
An Azure account is an identity in Azure Active Directory (Azure AD) or a directory that's trusted by Azure AD, such as a work or school account.
Resource Tag
- Each resource tag has a name and a value.
- Names must be 512 characters or less(124 for storage accounts), values must be 256 characters or less.
- Names can't contain: <, >, %, &, \, ?, /
- Limit of 50 tag name/value pairs for each resource, resource group, or subscription.
- Tag values can be JSON strings. The string can contain many values apply to a single name.
- The tag name remains constant for all resources that have the tag applied.
- The tag value can be selected from a defined set of values, or unique for a specific resource instance.
- A resource or resource group can have a maximum of 50 tag name/value pairs.
- Tags applied to a resource group aren't inherited by the resources in the resource group.
Cost Saving
- Reservations
- Azure Hybrid Benefits
- Azure Credits
- Azure Regions
- Budgets
- Pricing Calculator
Configure Azure Policy
Azure Policy is a service in Azure that enables you to create, assign, and manage policies to control or audit your resources.
Management Groups
Azure management groups provide a level of scope and control above your subscriptions.
- By default, all new subscriptions are placed under the top-level management group, or root group.
- All subscriptions within a management group automatically inherit the conditions applied to that management group.
- A management group tree can support up to six levels of depth.
- Azure role-based access control authorization for management group operations isn't enabled by default.
Create Policies
A policy definition describes the compliance conditions for a resource, and the actions to complete when the conditions are met.
One or more policy definitions are grouped into an initiative definition, to control the scope of your policies and evaluate the compliance of your resources.
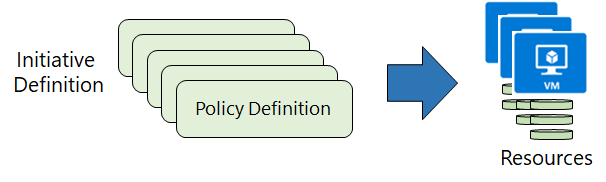
- Step 1: Create policy definitions
- Step 2: Create an initiative definition
- Step 3: Scope the initiative definition
- Step 4: Determine compliance
Policy Initiatice
An initiative definition has one or more policy definitions.
One example for using initiative definitions is to ensure your resources are compliant with security regulations.
Common Use Cases
- Implementing Governance
- Regulatory compliance like GDPR/HIPAA/PCI DSS
- Security
- Cost
- Management
Azure Policy Effects
Tip
The order of evaluation of the policy effect: Disabled -> Append/Modify -> Deny -> Audit.
- The Disable effect is always evaluated first to decide whether the rule should be evaluated afterwards.
- The Append effect does not modify the value of an existing field in a resource.
- The Append effect adds additional fields during the creation or update of a resource.
- If the field already exists in the resource and the values in the resource and the policy are different, then the policy acts as a deny and reject the requests.
- The Audit effect will create a warning event in the activity log for non-compliant resources.
- The Audit effect is evaluated last, before the Resource Provider handles a create or update request.
- You typically use the audit effect when you want to track non-compliant resources.
- The DeployIfNotExists effect is only evaluated if the request executed by the Resource Provider returns a success status code.
- Once the effect has been evaluated, it is triggered if the resource does not exist or if the resource defined by ExistenceCondition is evaluated as false.
Definition Structure
{
"properties": {
"displayName": "Allowed locations",
"description": "This policy enables you to restrict the locations your organization can specify when deploying resources.",
"mode": "Indexed",
"metadata": {
"version": "1.0.0",
"category": "Locations"
},
"parameters": {
"allowedLocations": {
"type": "array",
"metadata": {
"description": "The list of locations that can be specified when deploying resources",
"strongType": "location",
"displayName": "Allowed locations"
},
"defaultValue": [ "westus2" ]
}
},
"policyRule": {
"if": {
"not": {
"field": "location",
"in": "[parameters('allowedLocations')]"
}
},
"then": {
"effect": "deny"
}
}
}
}
- Mode
all: evaluate resource groups, subscriptions, and all resource typesindexed: only evaluate resource types that support tags and location- indexed should be used when creating policies that enforce tags or locations
Configure Role-Based Access Control
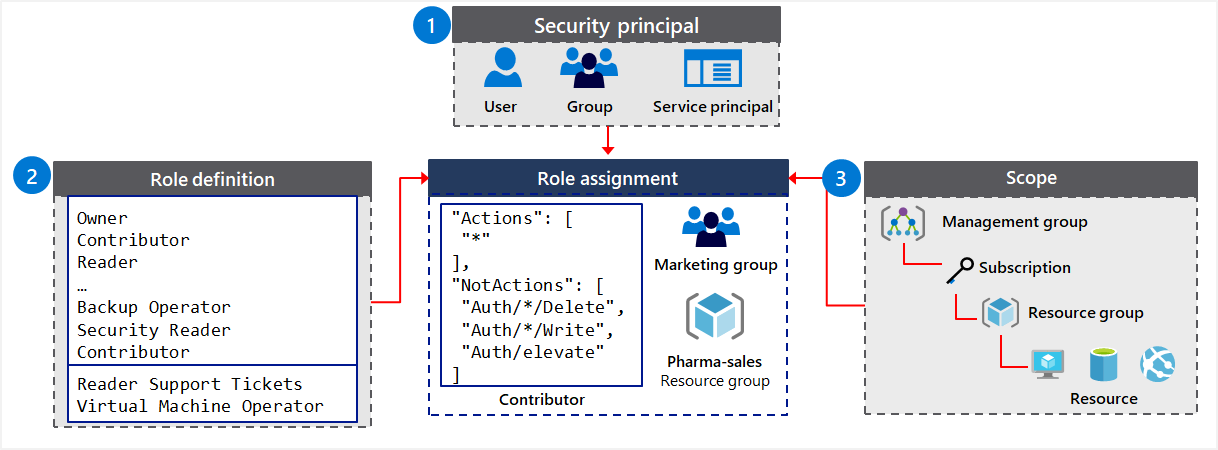
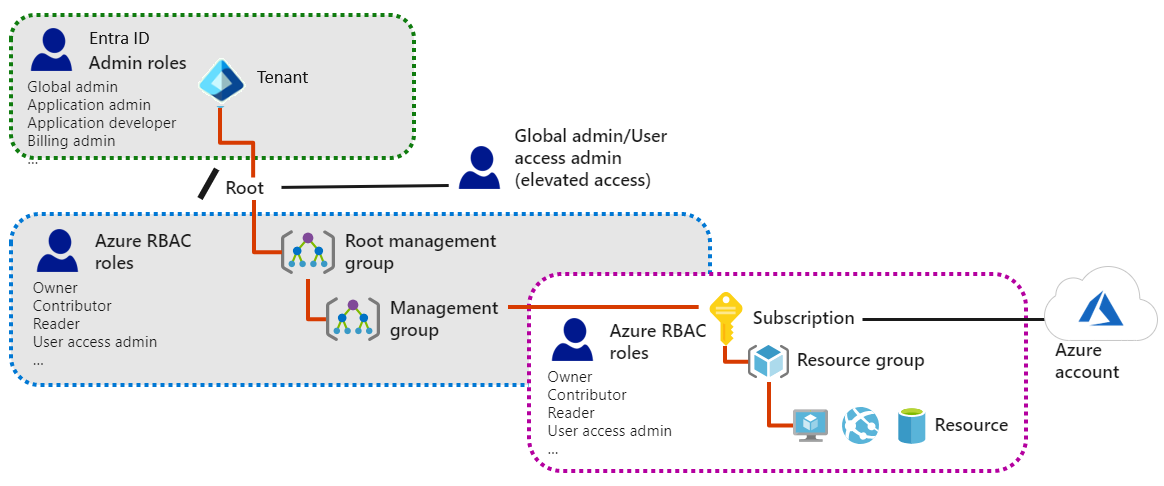
Role-based access control (RBAC) helps you manage who has access to Azure resources, what they can do with those resources, and what areas they have access to.
- Security principal:
- Object that represents something that is requesting access to resources.
- Examples: user, group, service principal, managed identity.
- Role definition:
- Collection of permissions that lists the operations that can be performed.
- Examples: Reader, Contributor, Owner, User Access Administrator.
- Scope:
- Boundary for the level of access that is requested.
- When you grant access at a parent scope, those permissions are inherited to the child scopes.
- In Azure, you can specify a scope at multiple levels: management group, subscription, resource group, or resource
- Examples: management group, subscription, resource group, resource.
- Assignment:
- Attaching a role definition to a security principal at a particular scope.
- Users can grant access described in a role definition by creating an assignment.
- Deny assignments are currently read-only and can only be set by Azure.
Note
Azure Resource Manager roles should be used instead of Classic administrator roles.
built-in roles
- Reader: Can view existing Azure resources.
- Contributor: Can create and manage all types of Azure resources, but can’t grant access to others.
- Owner: Has full access to all resources, including the right to delegate access to others.
-
User Access Administrator: Lets you manage user access to Azure resources.
-
Co-Administrator: a classic subscription role that is equivalent to the Owner Role-Based Access Control role.
-
User Administrator: an Azure AD administrator that does not control access to any Azure resources.
-
Deny Assignments
- Similar to windows deny files permission
- Blocks users from performing specific actions even if a role assignments allows it
- Can only be created using Azure Blue Prints or managed apps
Azure Roles vs Azure Active Directory Roles
- Azure RBAC roles:
- Manage access to Azure resources.
- Scope can be specified at multiple levels (management group, subscription, resource group, resource).
- Role information can be accessed in Azure portal, Azure CLI, Azure PowerShell, Azure Resource Manager templates, REST API.
- Azure AD roles:
- Manage access to Azure Active Directory resources.
- Scope is at the tenant level.
- Role information can be accessed in Azure admin portal, Microsoft 365 admin portal, Microsoft Graph AzureAD PowerShell.
Create Azure users and groups in Azure Active Directory
A user's account access consists of the type of user, their role assignments, and their ownership of individual objects.
Implement and Manage Storage in Azure
Configure storage accounts
Azure Storage Categories
- Storage for Virtual Machines
- Virtual machine storage includes disks and files.
Disksare persistent block storage for Azure IaaS virtual machines.Filesare fully managed file shares in the cloud.
- Unstructured Data
- Unstructured data includes Blobs and Data Lake Store.
Blobsare highly scalable, REST-based cloud object store.Data Lake Storeis Hadoop Distributed File System (HDFS) as a service.
- Structured Data
- Structured data includes Tables, Cosmos DB, and Azure SQL DB.
Tablesare a key/value, autoscaling NoSQL store.Cosmos DBis a globally distributed database service.Azure SQL DBis a fully managed database-as-a-service built on SQL.
Storage Account Tiers
- Standard
- backed by magnetic drives (HDD) and provide the lowest cost per GB
- use cases: applications that require bulk storage or where data is infrequently accessed.
- Premium
- backed by solid-state drives (SSD) and offer consistent low-latency performance
- use cases: Azure virtual machine disks with I/O-intensive applications, like databases.
Note
You can't convert a Standard storage account to a Premium storage account or vice versa.
You must create a new storage account with the desired type and copy data, if applicable, to a new storage account.
Storage Services
- Azure Containers (Blobs): A massively scalable object store for unstructured text and binary data.
- Azure Files(Directories): Managed file shares for cloud or on-premises deployments.
- Azure Queues(Entities): A messaging store for reliable messaging between application components.
- Azure Tables(Messaging): A NoSQL store for schema-less storage of structured data.
Access Keys
The order of operations to rotate storage account access keys:
- Update connection string with secondary access key
- Regenerate primary access key
- Update connection string with primary access key
- Regenerate secondary access keys
Azure Data Redundancy
- Protect your data from hardware failures, network or power outages, and massive natural disasters.
- Even in the event of a failure, redundancy ensures your storage account's availability and durability.
- Tradeoffs between lower costs and higher availability
- Redundancy in the primary region
- Locally redundant storage (LRS) – Three synchronous copies in same data center
- Zone-redundant storage (ZRS) – Three synchronous copies in three availability zones (AZs)
- Redundancy in a secondary region
- Geo-redundant storage (GRS) – LRS + Asynchronous copy to secondary region
- Geo-zone-redundant storage (GZRS)
- With GRS or GZRS, the data in the secondary region isn't available for read or write access unless there is a failover to the secondary region.
-
For read access to the secondary region, configure your storage account to use
- Read-access geo-redundant storage (RA-GRS)
- Read-access geo-zone-redundant storage (RA-GZRS).
-
Locally redundant storage (LRS) – Three synchronous copies in same data center
- Zone-redundant storage (ZRS) – Three synchronous copies in three availability zones (AZs)
- Geo-redundant storage (GRS) - LRS + Asynchronous copy to secondary region (three more copies using LRS) – Read only access
- Read-access geo-redundant storage (RA-GRS) – Read Access on GRS
- Geo-zone-redundant storage (GZRS) – ZRS + Asynchronous copy to secondary region (three more copies using LRS) – Read only access
- Read-access geo-zone-redundant storage (RA-GZRS) – Read Access on GZRS
Note
The only two methods that support LRS to ZRS migrations are to perform a manual migration of the data or to request a live migration.
However, live migration is not supported when you are migrating Azure Files Network File System version 4.1(NFSv4.1)
Configure Blob Storage
Blob service resources
Blob storage offers three types of resources:
- The storage account
- Containers in the storage account
- Blobs in a container
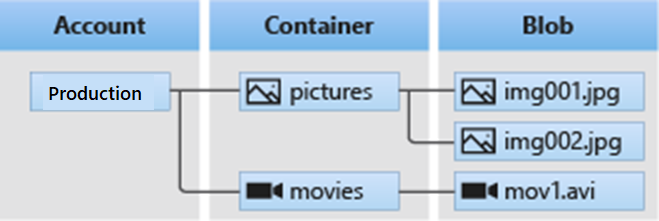
Tip
All blobs must be in a container.
An account can contain an unlimited number of containers.
A container can store an unlimited number of blobs.
Public access level
Specifies whether data in the container may be accessed publicly.
By default, container data is private to the account owner.
- Use Private to ensure there is no anonymous access to the container and blobs.
- Use Blob to allow anonymous public read access for blobs only.
- Use Container to allow anonymous public read and list access to the entire container, including the blobs.
Blob access tier
- Hot.
- The Hot tier is optimized for frequent access of objects in the storage account.
- New storage accounts are created in the Hot tier by default.
- Cool.
- The Cool tier is optimized for storing large amounts of data that is infrequently accessed and stored for at least 30 days.
- Storing data in the Cool tier is more cost-effective, but accessing that data may be more expensive than accessing data in the Hot tier.
- Archive.
- The Archive tier is optimized for data that can tolerate several hours of retrieval latency and will remain in the Archive tier for at least 180 days.
- The Archive tier is the most cost-effective option for storing data, but accessing that data is more expensive than accessing data in the Hot or Cool tiers.
Tip
The Cool access tier is optimal for storing data for long periods of time at low cost, with the data always being available immediately when needed.
Lifecycle management
- Transition blobs to a cooler storage tier (hot to cool, hot to archive, or cool to archive) to optimize for performance and cost.
- Delete blobs at the end of their lifecycles.
- Define rules to be run once per day at the storage account level.
- Apply rules to containers or a subset of blobs.
Object replication
- Object replication requires that blob versioning is enabled on both the source and destination accounts, and that blob change feed is enabled for the source account.
- The change feed provides transaction log support for changes made to blobs and blob metadata in your source storage account
- Blob Versioning is necessary to automatically maintain previous versions of blob objects
- Object replication doesn't support blob snapshots. Any snapshots on a blob in the source account are not replicated to the destination account.
- Object replication is supported when the source and destination accounts are in the hot or cool tier. The source and destination accounts may be in different tiers.
- When you configure object replication, you create a replication policy that specifies the source storage account and the destination account.
- A replication policy includes one or more rules that specify a source container and a destination container and indicate which block blobs in the source container will be replicated.
Types of blobs
- block blobs (default)
- consist of blocks of data assembled to make a blob.
- Most scenarios using Blob storage employ block blobs.
- Block blobs are ideal for storing text and binary data in the cloud, like files, images, and videos.
- page blobs
- can be up to 8 TB in size and are more efficient for frequent random read/write operations.
- Azure virtual machines use page blobs as OS and data disks.
- append blobs
- like block blobs in that they are made up of blocks, but they are optimized for append operations, so they are useful for logging scenarios.
- When you modify an append blob, blocks are added to the end of the blob only
- Updating or deleting of existing blocks is not supported
Note
Once the blob has been created, its type cannot be changed.
Configure storage security
A shared access signature (SAS) is a URI that grants restricted access rights to Azure Storage resources.
You can provide a SAS to clients who shouldn't have access to your storage account key.
A SAS token:
- Grants secure and delegated access to resources in Azure Storage Account
- Provides access to clients without sharing their storage account keys
- Provides access to Azure resources in multiple storage services
- Delegates secured access to a resource in only one of the storage services
Note
The default network rule is to allow all connections from all networks.
Azure Table Storage
- NoSQL key-value Storage
- Items are referred to as rows, and fields are known as columns
- All rows in a table must have a key
- No concept of relationships, stored procedures, secondary indexes, or foreign keys
- Data will usually be denormalized
- To help ensure fast access, Azure Table Storage splits a table into partitions
- Support very large volume of Data
- Consider Cosmos DB for new development
- Advantages
- It's simpler to scale
- A table can hold semi-structured data
- No complex relationships
- Data insertion and retrieval is fast
- Good to use for:
- Storing TBs of structured data capable of serving web scale applications
- Storing datasets that don't require complex joins, foreign keys, or stored procedures, and that can be denormalized for fast access.
- Capturing event logging and performance monitoring data.
Azure Queue Storage
- Store large numbers of messages.
- Access messages via authenticated calls using HTTP or HTTPS.
- May contain millions of messages, up to the total capacity limit of a storage account.
- Queues are commonly used to create a backlog of work to process asynchronously.
Azure Disk Storage
- VM uses disks as a place to store an operating system, applications, and data in Azure.
- One virtual machine can have one OS disk and multiple Data disk but one data disk can only be link with one VM.
- Both the OS disk and the data disk are virtual hard disks (VHDs) stored in an Azure storage account.
- The VHDs used in Azure is .vhd files stored as page blobs in a standard or premium storage account in Azure.
- Unmanaged disks: We can create a storage account and specify it when we create the disk.
- Not recommended, previous unmanaged disks should migrate to managed disk
- Managed disk
- Azure creates and manages storage accounts in the background.
- We don't have to worry about scalability issues.
- Azure creates and manages the disk for us based on the size and performance tier we specify.
- Managed Disk types:
- Standard HDD: Backup, non-critical, infrequent access
- Standard SSD: lightly used production applications or dev/test environments
- Premium SSD disks: Super fast and high performance, very low latency, recommended for production and performance sensitive workloads
- Ultra disks (SSD): for most demanding IO-intensive workloads such as SAP HANA, top tier databases (for example, SQL, Oracle), and other transaction-heavy workloads
Benefits
- Highly available (three replicas)– 99.999% availability
- Scalable – 50,000 VM disks
- Granular access control - Use RBAC to assign specific permissions for a managed disk to one or more users.
- Integration with availability sets and Availability Zones, Backups and so on
Security
- Private links – allow you to generate SAS token
- Encryption
- Server-side encryption – data encryption-at-rest, default
- Azure Disk encryption - encrypt the OS and Data disks
Disk Roles
- OS Disk – Pre-installed OS, contain boot volume
- Data Disk – Store application data
- Temporary Disk
- Short-term storage for applications and processes
- May be lost during a maintenance or redeploy.
- Successful reboot will persist data.
Tip
You can remove a disk as long as nothing is actively using the disk when it is detached
Latency VS IOPS VS Throughput
- Latency is a time taken to respond to an I/O request
- IOPS is a unit of measurement for the number of read and write operations performed per second.
- Number of read write operations mostly useful for OLTP transactions used in Azure for DBs like SQL Server.
- Latency is proportional to IOPS
- Throughput refers to the quantity of data read or written per second.
- Measured in MB per second
- Mainly a unit for high data transfer applications like big data Hadoop, Kafka streaming
Snapshot
- A snapshot is a full, read-only copy of a virtual hard disk (VHD).
- You can take a snapshot of both operating system (OS) or data disk VHDs.
- Use Case:
- Point-in-time backup
- Restore or rebuild a VM
- Troubleshoot virtual machine (VM) issues
Azure Shared Disks
- Allow you to attach a managed disk to multiple virtual machines (VMs) simultaneously.
- Only ultra disks, premium SSDs, and standard SSDs can enable shared disks(No HDD)
- Shared managed disks do not come with a fully managed file system accessible through SMB/NFS.
- Use a cluster manager like Windows Server Failover Cluster (WSFC) or Pacemaker to handle cluster node communication and write locking.
Managed Disk VS Unmanaged Disk
- Managed Disks
- Managed by Azure
- High availability, secure
- Azure create storage account behind the scene
- Un-managed Disks
- Not Managed by Azure
- You create storage account
- Full control over data
- You have to take care of encryption, data recovery plans etc.
- You cannot create both managed and unmanaged disks on a VM
Disk Encryption
- Server-Side Encryption(SSE)
- Encrypts your disks at the storage account level, at rest.
- Default, always enabled, can’t turn off.
- Protect the data on OS and data disks. Temporary disks are not encrypted.
- Does not impact the performance of managed disks.
- Azure Disk Encryption(ADE)
- Encrypts your disks at the VM OS level.
- Use BitLocker for Windows VMs and DM-Crypt for Linux VMs.
- Data encrypt during transit
- Temporary disk and OS/data disk caches are also encrypted
- Requires an Azure Key Vault to control and manage disk encryption keys and secrets
- Key vault and VMs must reside in the same Location and subscription
- Encryption at host(EAH)
- End-to-end encryption between the disk as rest and when the disk is allocated to and ran on a host.
- Also encrypt your temporary disk and cache at host.
- Does not use your VM's CPU and doesn't impact your VM's performance.
- Truly end-to-end encryption
- Prerequisite: must enable the feature for your subscription
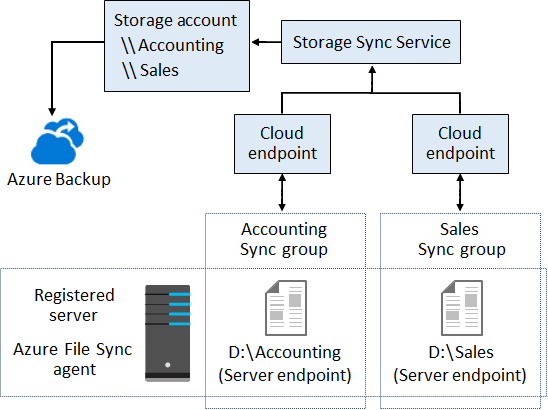
Configure Azure files storage and Azure File Sync
- Enables you to create files shares in the cloud, and access these file shares from anywhere with an internet connection
- Mounted concurrently by cloud or on-premises deployments.
- Accessible from Windows, Linux, and macOS clients.
- Accessible Server Message Block (SMB) protocol or Network File System (NFS) protocol
- Azure Files ensures the data is encrypted at rest, and the SMB protocol ensures the data is encrypted in transit.
Common uses of file storage
- replace and supplement
- access anywhere
- lift and shift
- azure file sync
- shared application
- diagnostic data
- tools and utilities
Cloud tiering allows frequently accessed files to be cached on the local server. Infrequently accessed files are tiered, or archived, to the Azure file share according to the policy created.
Key Benefits
- Shared access: Replace on-premises file shares with Azure file shares without application compatibility issues
- Fully managed: Azure will manage hardware or an OS
- Resiliency: you don’t have to deal with local power and network issues.
Managing file share
- File share quotas
- Windows - ensure 445 port(Server Message Block(SMB) protocol) is open - Error 67 is returned when this port is blocked
- Linux / MacOS - mount the drive
- Secure transfer required - SMB 3.0 encryption
Note
Azure File currently allows you to mount a share to Windows Server 2019 and above
file sync components
Configure storage with tools
Azure Storage Explorer
Azure Storage Explorer is a standalone app that makes it easy to work with Azure Storage data on Windows, macOS, and Linux.
- With Storage Explorer, you can access multiple accounts and subscriptions and manage all your storage content.
- Create, delete, view, and edit storage resources
- View and edit Blob, Queue, Table, File, Cosmos DB storage, and Lake Storage
- Obtain shared access signature(SAS) keys
Use the import and export service
Azure Import/Export service is used to securely import large amounts of data to Azure Blob storage and Azure Files by shipping disk drives to an Azure datacenter.
Import jobs: transfers large amounts of data to Azure Blob storage (block and page blobs) and Azure Files by shipping disk drives to an Azure datacenter.

Export jobs: transfer data from Azure storage to hard disk drives and ship to your on-premise sites.

The Azure Import/Export Tool is the drive preparation and repair tool that you can use with the Microsoft Azure Import/Export service.
Use AzCopy
AzCopy v10 is the next-generation command-line utility for copying data to/from Microsoft Azure Blob and File storage, which offers a redesigned command-line interface and new architecture for high-performance reliable data transfers.
- The AzCopy tool can work with two different storage accounts.
- Authentication options include Active Directory or SAS token
Tip
AzCopy is available on Windows, Linux, and macOS.
Note
Authorize AzCopy:
- Blob storage: Azure AD & SAS
- File storage: SAS only
Create an Azure Storage account
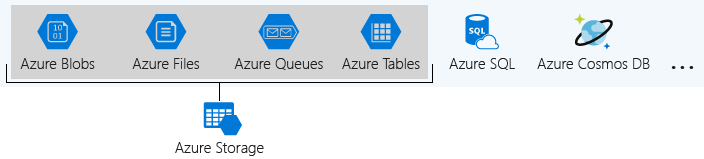
A storage account is a container that groups a set of Azure Storage services together.
Storage account settings
A storage account defines a policy that applies to all the storage services in the account.
The settings that are defined by a storage account are:
- Subsription
- Location
- Performance
- Replication
- Access tier
- Secure transfer required
- Virtual networks
Account Settings
- Name
- globally unique within Azure
- use only lowercase letters and digits and be between 3 and 24 characters
- Deployment model
- Resource Manager: the current model that uses the Azure Resource Manager API
- Classic: a legacy offering that uses the Azure Service Management API
- Account kind
- StorageV2 (general purpose v2): the current offering that supports all storage types and all of the latest features
- Storage (general purpose v1): a legacy kind that supports all storage types but may not support all features
- Blob storage: a legacy kind that allows only block blobs and append blobs
Note
You cannot convert a Storage/StorageV2 account to a premium storage account
You can convert a Storage account to StorageV2 account
Access Keys
Steps to update storage account key:
- Step1: Update App using secondary key
- Step2: Regenerate primary key
- Step3: Update App using new primary key
- Step4: Regenerate secondary key
Control access to Azure Storage
Access Azure Storage Methods
- Public access
- Azure Active Directory (Azure AD)
- Shared key
- Shared access signature (SAS)
Authorization
Deploy and manage Azure compute resources
Configure virtual machines
VM size
- A Series: Entry-level for dev/test
- B Series: Economical bursting
- D Series: General purpose compute
- Dc Series: Protect data in use
- E Series: In-memory, hyper-threaded applications optimized
- F Series: Compute optimized
- G Series: Memory and storage optimized
- H Series: High performance computing
- L Series: Storage optimized
- M Series: Memory optimized
- Mv2 Series: Large memory optimized
- N Series: GPU enabled
VM storage
All Azure virtual machines have at least two disks – an operating system disk and a temporary disk.
Virtual machines also can have one or more data disks. All disks are stored as VHDs(virtual hard disk).
Temporary disk:
- On Windows virtual machines, this disk is labeled as the
D:drive by default and it used for storingpagefile.sys. - On Linux virtual machines, the disk is typically
/dev/sdband is formatted and mounted to/mntby the Azure Linux Agent.
Note
Don’t store data on the temporary disk. It provides temporary storage for applications and processes and is intended to only store data such as page or swap files.
Managed disks: Azure-managed disks are stored as page blobs, which are a random IO storage object in Azure.
VM Images
Image: a copy of the full VM (include OS and data disks)
- After you build and customize a virtual machine, you can save the new image as a set of VHDs.
- You can put this new image in to Azure compute gallery.
- Two types of Images
- Specialized VM images
- Copy of a live virtual machine
- Copy of the configured operating system, software, user accounts, databases, connection information, and other data for your system.
- Use as a backup of your system at a particular point in time, you can restore your virtual machine from this image a
- New VM created out of image will have same host name, user accounts, and other settings
- Generalized VM Images
- No information retained.
- Original VM is unusable after you perform the process
- Tools for preparing a virtual machine for generalization
- For Windows, use the Microsoft System Preparation (Sysprep) tool.
- For Linux, use the Windows Azure Linux Agent (waagent) tool.
- Specialized VM images
Configure virtual machine availability
Setup availability sets
An Availability Set is a logical feature used to ensure that a group of related VMs are deployed so that they aren't all subject to a single point of failure and not all upgraded at the same time during a host operating system upgrade in the datacenter.
Configure scale sets:
- Instance count(number of VMs in the scale set - 0 to 1000)
- Instance size(size of each virtual machine in the scale set)
- Usage of managed disks
- Scaling beyong 100 instances
Tip
In Azure, you can assign a VM to an availability set only during initial deployment
Work Mechanism
- Each availability set can be configured with up to three fault domains and twenty update domains
- These configurations can't be changed once the availablity set has been created
- Update domain indicate groups of virtual machines and underlying physical hardware that can be rebooted at the same time
- Fault domain define the group of virtual machines that share a common power source and network switch
Configure virtual machine extensions
Azure virtual machine extensions are small applications that provide post-deployment configuration and automation tasks on Azure VMs.
Azure VM extensions can be:
- Managed with Azure CLI, PowerShell, Azure Resource Manager templates, and the Azure portal.
- Bundled with a new VM deployment or run against any existing system.
Implement custom script extensions
A Custom Script Extension(CSE) can be used to automatically launch and execute virtual machine customization tasks post configuration.
Tip
Custom script extensions will time out after 90 minutes and that should be considered when deciding on the scope of the script.
Implement desired state configuration
Desired State Configuration (DSC) is a management platform in Windows PowerShell.
- DSC enables deploying and managing configuration data for software services and managing the environment in which these services run.
- DSC provides a set of Windows PowerShell language extensions, Windows PowerShell cmdlets, and resources that you can use to declaratively specify how you want your software environment to be configured.
- DSC also provides a means to maintain and manage existing configurations.
Configure Azure App Services
Azure App Service is an HTTP-based service for hosting web applications.
Applications run and scale with ease on both Windows and Linux-based environments.
- Enables you to host and manage your web applications
- Platform as a service (PaaS) environment
- Focus on the business value and logic
- Azure handles the infrastructure
- Automatic scaling and high availability
- Programming language of your choice
- Supports Windows and Linux
- Automated deployments from GitHub or Azure DevOps
- Pay only for compute resources your app uses
- App Service plan determines how much hardware is devoted to your application
Types of App Service
- Web apps
- Full support for hosting websites and web applications
- Language: ASP.NET, ASP.NET Core, Java, Ruby, Node.js, PHP, or Python.
- Operating System: Windows or Linux
- Web apps for containers can host your existing container images.
- API apps
- Build REST-based web APIs
- Choice of language and framework
- Can be consumed from any HTTP- or HTTPS-based client.
- WebJobs
- Run a program (.exe, Java, PHP, Python, or Node.js)
- Run a script (.cmd, .bat, PowerShell, or Bash)
- Can be scheduled or run by a trigger
- Often used to run background tasks as part of your application logic.
- Mobile apps
- Quickly build a back end for iOS and Android apps
- Store mobile app data in a cloud-based SQL database.
- Authenticate customers against common social providers, such as MSA, Google, Twitter, and Facebook.
- Send push notifications.
- Execute custom back-end logic in C# or Node.js.
App Service Backup
- App configuration, file content and database connected to your app
- Can backup manually or scheduled
- Can perform partial and full backups
- Backups are visible on the containers page of storage account
- Must have standard premium or isolated app service plan
- Must have an azure storage account and container in same subscription account
- Backups max out at 10GB of app and database content
- Backups of TLS enabled Azure Database for MySQL and PostgreSQL are not supported.
- lets you easily create app backups manually or on a schedule.
- Can restore the app by overwriting the existing app or restoring to another app.
- Backup files store in storage account in same subscription.
- What gets backed up: App configuration, file content and database connected to your app
- Must have standard premium or isolated app service plan
- Backups can be up to 10 GB of app and database content.
- Backups of TLS enabled Azure Database for MySQL and PostgreSQL are not supported.
- Partial backups are supported. Partial backups allow you choose exactly which files you want to back up.
- Using a firewall enabled storage account as the destination for your backups is not supported.
Deployment Settings
- You can test and validate changes in staging deployment slot before pushing them to production slot.
- After validation, you can simply swap staging and production slot.
- There is no downtime in this swap. No requests are lost due to traffic redirection.
- If rollback required, simply swap again.
- When pre-swap validation is not required, Auto Swap can be configured to automate the whole workflow.
Security
- Deployment slots are live apps with their own hostnames.
- App content and configurations elements can be swapped between two deployment slots.
- Stage deployment slots allow you to test changes before deploying to production.
- Pre-warming a slot before deploying an app ensures that all instances of the slot are ready to go. Deploying your app without downtime. No requests are lost due to traffic redirection.
- When pre-swap validation is not required, Auto Swap can be configured to automate the whole workflow.
- After a swap, the previously staged app is now the production app. To restore your “last known good site” if the changes swapped into production do not meet your expectations, simply perform the same swap.
- Automated swapping simplifies Azure DevOps scenarios that require no cold starts or downtime for app users.
- When auto swap from a source slot to production is enabled, App Service automatically swaps the app into production after it has warmed up in the source slot.
- Web apps on Linux don't support auto swap yet.
Service Plan
- Shared: designed for development and testing, does not support autoscale and only allow 1 instance
- Basic: does not support autoscale and is limited to 3 instances
- Standard: support autoscale, limited to no more than 10 instances
- Premium: support autoscale with up to 30 instances
Managing App Service
- Create App Service
- Give unique name
- Access azurewebsites.net to map to a custom domain
- Publish code or docker container and runtime stack
- Select the operating system
- Select the region closest to your user
- Choose the app service plan
- Secure App Service
- Sign in with a third-party identity provider
- Troubleshoot with Diagnostic Logs
- Add SSL certificate-HTTPS
- Define the priority ordered allow/deny list
- Stores secret in Azure Key Vault
- Configure custom domain names
- Redirect default web app for URL
- Validate custom domain in Azure
- Use DNS registry for domain provider to create CNAME
- Ensure that the app service plan is supported by the custom domains
- Configure backup
- Create backups for apps on a schedule or manully
- Create backup for the configuration, database, and file content
- Requires Standand/Premium plan
- Configure partical plan
- Restore app to a previous state, on-demand
- Configure networking settings
- Create gateway subnet
- Create virtual network gateway
- Create local network gateway
- Create VPN connection
- Enable inbound traffic to Azure
- Configure deployment settings
- Configure app settings and connections to stick to a slot and not be swapped
- Explore creating a new settings for the web app
Configure Azure Container Instances(ACI)
Implement container groups
The top-level resource in Azure Container Instances is the container group.
A container group is a collection of containers that get scheduled on the same host machine.
The containers in a container group share a lifecycle, resources, local network, and storage volumes.
It's similar in concept to a pod in Kubernetes.
Note
You cannot deploy a container group on a subnet that already contains resources such as VMs.
You can deploy a container group on a subnet that already hosts a container group, a subnet that does not host any resources, or you can recreate a new subnet when you create the container group.
Azure container instances
Features:
- Fast Startup Times(in seconds)
- Public IP Connectivity and DNS Names
- Hypervisor-level Security
- Custom Sizes
- Persistent Storage
- Linux and Windows Containers
- Co-scheduled Groups
- Virtual Network Deployment
Configure Azure Kubernetes Service
AKS terminology

- Pools are groups of nodes with identical configurations.
- Nodes are individual virtual machines running containerized applications.
- Master Node/ Control Planes controls and manages the whole Kubernetes system.
- API server is like the front end to the control plane in your Kubernetes cluster.
- Scheduler is the component that's responsible for the assignment of workloads across all nodes.
- etcd - key-value store.
- Controllers track the state of objects in the cluster.
- Worker Node run the actual applications that you deploy.
- Kubelet - monitors work requests from the API server
- kube-proxy - handle routing and load balancing of traffic
- Container runtime - runtime is responsible for fetching, starting, and stopping container images.
- Pods are a single instance of an application. A pod can contain multiple containers.
- Container is a lightweight and portable executable image that contains software and all of its dependencies.
- Deployment has one or more identical pods managed by Kubernetes.
- Manifest is the YAML file describing a deployment.
- The kubelet is the Kubernetes agent that processes the orchestration requests from the Azure-managed node.
AKS networking
- Cluster IP
- Creates an internal IP address for use within the AKS cluster.
- Good for internal-only applications that support other workloads within the cluster.
- NodePort
- Creates a port mapping on the underlying node that allows the application to be accessed directly with the node IP address and port.
- LoadBalancer
- Creates an Azure load balancer resource, configures an external IP address, and connects the requested pods to the load balancer backend pool.
- To allow customers traffic to reach the application, load-balancing rules are created on the desired ports.
- ExternalName
- Creates a specific DNS entry for easier application access.
AKS storage
- Volume
- Represents a way to store, retrieve, and persist data across pods and through the application lifecycle.
- Can be created manually or have Kubernetes automatically create them.
- Persistent volumes
- Storage resource created and managed by the Kubernetes API
- Can exist beyond the lifetime of an individual pod.
- Azure Disks or Azure Files
- Can be statically created by a cluster administrator, or dynamically created by the Kubernetes API server.
- Storage classes
- Define different tiers of storage, such as Premium and Standard
- Defines the reclaimPolicy
- Persistent volume claims
- A user's request for storage is called a PersistentVolumeClaim.
- Requests storage of a particular StorageClass, access mode, and size
- It looks like a pod. Node resources are consumed by pods, and PersistentVolume resources are consumed by PersistentVolumeClaims.
- Pods have the ability to request specific resource levels (CPU and Memory).
- Claims can specify a specific size and mode of access (for example, once read/write or many times read-only).
Scaling in AKS
- Scaling – as workload increase/decrease, you may need to increase/decrease infrastructure in terms of pods and nodes
- Manually scale
- Scale Pods
- Scale Nodes
- Horizontal pod autoscaler (HPA)
- Monitor the resource demand and automatically scale the number of replicas
- Define the minimum and maximum number of replicas that can run
- Define the metric to monitor like CPU usage
- Cluster autoscaler
- Adjusts the number of nodes based on the requested compute resources in the node pool
- Scale out events – increase number of nodes because of node pool resource constraints
- Scale in events – decreases the number of nodes because node pool has more compute resources than are required
ACI VS AKS
- ACI
- A service that lets you deploy containers on Azure without having to maintain or patch the environment.
- Basic web applications, DevTest scenarios, and batch processing are all supported by ACI.
- When you just need to run a few containers, it's a perfect option.
- Limited scalability and low availability
- Managed environment
- Only pay for containers
- Deployment is easy.
- AKS
- Alternatively, For more complex container designs where you require additional control over the health and performance of your containers, you may utilize Azure Kubernetes Service (AKS).
- You can coordinate the deployment, update, and management operations for all of your containers using AKS.
- If you need to operate tens, hundreds, or even thousands of containers, the AKS Open source project could be a good fit.
- It's one tool in a class of tools called container orchestrators
Configure and manage virtual networks for Azure administrators
Network Knowledge
Private IP Address
- For setting up private networks, three IP address ranges have been reserved by internet Assigned Numbers Authority (IANA)
- Class A – for large organization
- Class B – Medium size organization
- Class C – home or small business
| Class | Private IP Address Range | Subnet Mask |
|---|---|---|
| A | 10.0.0.0 - 10.255.255.255 | 255.0.0.0 |
| B | 172.16.0.0 - 172.16.31.255 | 255.255.0.0 |
| C | 192.168.0.0 - 192.168.255.255 | 255.255.255.0 |
Subnet Mask
- In IP address = Network address + Host Address
- The Subnet Mask specifies which part of the IP address corresponds to the network and which part corresponds to the host, by masking the network portion of the IP address.
CIDR Notation
- Classless inter domain routing (Slash notation)
- It’s a shorter way to write a subnet mask.
- “Slash” notation tells you how many bits are associated with Subnet Mask.
Network Interface Card(NIC)
- A network interface card (NIC) is a piece of hardware that allows a computer to connect to a network.
- Network Interface Card (NIC) also called:
- Network Interface Controller
- Network Adapter
- LAN Adapter
- Can be:
- Wired
- Wireless
- A network interface enables an Azure Virtual Machine to communicate with internet, Azure, and on-premises resources.
- When you create VM using portal, one NIC with default setting created.
- IP address and NSG rules are attach with NIC
- You can create more than one NIC and attach to VM.
Terminology
- Switch: connects devices within same network
- Router: a networking device that forwards data packets between different computer networks
- Subnet: defines your local area network range
- Gateway: the IP Address of the router
- NAT: Network address translation is a method of remapping an IP address while they are in transit across a traffic routing device
- Firewall: set of passive rules to protect network from unauthorized access
- DMZ: demilitarized zone is a subnetwork that contains and exposes a device to an untrusted network such as Internet
- Port Forwarding: redirects a communication request from one address and port number combination to another while the packets are traversing a network gateway
Configure virtual networks
An Azure Virtual Network (VNet) is a representation of your own network in the cloud. It is a logical isolation of the Azure cloud dedicated to your subscription.
- Your own isolated network in Azure.
- Region can have multiple VNets but each VNet belong to same Region
- Within a VNet, network traffic is isolated (not visible) from network traffic in all other Azure VNet.
- You maintain complete control over all traffic entering and leaving a VNet.
- IP Address is a address of resource which ensures the traffic gets to the right server on the internet
- Every resource gets its own unique IP Address on that Vnet within the address space.
- Scaling – You can add more VNets or more addresses on existing VNet.
VNet Subnets
- Organize and group resources on subnets
- Separate public and private resources into distinct subnets
- Resources in a public subnet CAN be accessed from internet
- Resources in a private subnet CANNOT be accessed from internet, but resources in a public subnet can connect with resources in a private subnet
- We can use network security groups to secure individual subnets
Azure reserve IP address
Azure reserves five IP addresses within each subnet:
x.x.x.0: Network addressx.x.x.1: Reserved by Azure for the default gatewayx.x.x.2,x.x.x.3: Reserved by Azure to map the Azure DNS IPs to the VNet spacex.x.x.255: Network broadcast address
Configure Network Security Groups(NSG)
A network security group contains a list of security rules that allow or deny inbound or outbound network traffic.
An NSG can be associated to a subnet or a network interface.
A network security group can be associated multiple times.
- NSG can filter incoming and outgoing traffic.
- NSG can contain set of security rules which can allow or deny traffic
- NSGs is like internal firewall inside your Virtual network
- Remember Azure firewall is an external firewall, outside your virtual network
- NSG is a basic network filtering and does not have features like FQDN and threat intelligence.
- NSG can be associated to one or multiple subnets or network interface (NIC)
- You can’t link NSG with VNet.
- OSI Layer 4 (5 properties or tuples)
- Source and Destination IP address
- Source and Destination port number
- Protocol
- Priority – lower number, higher priority
network security group rules
- Name
- Priority
- Port
- Protocol (Any, TCP, UDP)
- Source (Any, IP Addresses, Service tag)
- Destination (Any, IP Addresses, Virtual Network)
- Action (Allow or Deny)
Service Tag
Service tags represent a group of IP addresses.
Service tags make it easy to aggregate IP address blocks that otherwise would require several network security group(NSG) rules to accomplish.
Valid service tag:
- VirtualNetwork
- Internet
- SQL
- Storage
- AzureLoadBalancer
- AzureTrafficManager
Application Security Group
- Application security group allows you to group virtual machines and define NSG rules on that group.
- Don’t need a manual maintenance of explicit IP addresses.
- ASGs introduce the ability to deploy multiple applications within the same subnet and also isolate traffic based on ASGs.
- If the VM is running more than one workloads, we can simply assign multiple ASGs.
Configure Azure Firewall
Azure Firewall is a managed, cloud-based network security service that protects your Azure Virtual Network resources.
It's a fully stateful firewall as a service with built-in high availability and unrestricted cloud scalability.
The Azure firewall uses a statically assigned public IP address.
- Azure Firewall goes from OSI layer 3 all the way up to layer 7
- NSG operates at OSI layer 4
- Firewall can also deal with DNS names, as well as ports, protocols, and IP addresses.
- Azure Firewall can function in a hybrid cloud
- All traffic that's going from your Azure infrastructure to on-premises has to go through the Azure Firewall
- The Azure firewall uses a statically assigned public IP address.
Features
- Built-in high availability.
- High availability is built in, so additional load balancers aren't required.
- There's nothing you need to configure.
- Availability Zones.
- Azure Firewall can be configured during deployment to span multiple Availability Zones for increased availability.
- Unrestricted cloud scalability.
- Azure Firewall can scale up as much as you need to accommodate changing network traffic flows, so you don't need to budget for your peak traffic.
- Application FQDN filtering rules.
- You can limit outbound HTTP/S traffic or Azure SQL traffic to a specified list of fully qualified domain names (FQDN) including wild cards.
- Network traffic filtering rules.
- You can centrally create allow or deny network filtering rules by source and destination IP address, port, and protocol.
- Azure Firewall is fully stateful, so it can distinguish legitimate packets for different types of connections. Rules are enforced and logged across multiple subscriptions and virtual networks.
- Threat intelligence.
- Threat intelligence-based filtering can be enabled for your firewall to alert and deny traffic from/to known malicious IP addresses and domains.
- The IP addresses and domains are sourced from the Microsoft Threat Intelligence feed.
- Multiple public IP addresses.
- You can associate multiple public IP addresses with your firewall.
Create Azure Firewalls

- The hub is a virtual network in Azure that acts as a central point of connectivity to your on-premises network.
- The spokes are virtual networks that peer with the hub, and can be used to isolate workloads.
- Traffic flows between the on-premises datacenter and the hub through an ExpressRoute or VPN gateway connection.
Create firewall rules
- Application rules:
- Configure fully qualified domain names (FQDNs) that can be accessed from a subnet.
- For example, specify the Windows Update network traffic through the firewall.
- Network rules:
- Similar like NSG
- Non-HTTP/S traffic must have a network rule to pass through the firewall.
- If resources one subnet must communicate with another, you would configure a network rule from source to destination.
- DNAT rules:
- Destination Network Address Translation (DNAT)
- Translate and filter inbound traffic to your subnets.
- Translate your firewall public IP and port to a private IP and port.
Note
By default, Azure Firewall blocks all traffic, unless you enable it.
Azure Firewall Manager
- Centrally manage Azure Firewalls across multiple subscriptions.
- Rule sets can be shared across multiple Azure Firewall instances.
- Can integrate with third-party services, like iboss, Zscaler, and CheckPoint, to provide additional firewall or enterprise class firewall functionality
- Can also integrate with the virtual WAN concept.
Configure Azure DNS
Azure DNS hosts the registered domains. Administrators can control and configure the domain records, like A, CNAME, MX, and set up alias records.
DNS Record Types
- A: the host record, and the most common type of DNS record. It maps the domain or host name to the IP address.
- A record set will not be automatically updated or deleted if the target record is modified or deleted
- A alias record set is a special type of record set that allows you to create an alternative name for a record set in your domain zone or for resources in your subscription
- CNAME: Canonical Name record that's used to create an alias from one domain name to another domain name.
- MX: the mail exchange record. It maps mail requests to your mail server, whether hosted on-premises or in the cloud.
- TXT: the text record. It's used to associate text strings with a domain name. Azure and Microsoft 365 use TXT records to verify domain ownership.
- Wildcards
- CAA (certificate authority)
- NS (name server)
- SOA (start of authority)
- SPF (sender policy framework)
- SRV (server locations)
- PTR(pointer): resolve an IP address to a hostname
Identify domains and custom domains
When you create an Azure subscription, an Azure AD domain is automatically created. This instance of the domain has an initial domain name in the form domainname.onmicrosoft.com.
The initial domain name is intended to be used until a custom domain name is verified.
Note
- You must be a global administrator to perform domain management tasks.The global administrator is the user who created the subscription.
- Domain names in Azure AD are globally unique. When one Azure AD directory has verified a domain name, other directories can't use that name.
- Before a custom domain name can be used by Azure AD, the custom domain name must be added to your directory and verified.
Azure Private DNS
Azure Private DNS manages and resolves domain names in a virtual network without adding a custom DNS solution.
- Private DNS manages and resolves domain names in the virtual network without the need to configure a custom DNS solution.
- By using private DNS zones, you can use your own custom domain name instead of the Azure-provided names during deployment.
- A private zone can be linked to one or more virtual networks by the use of virtual networks links
- Auto-registration – This allows VM’s to be automatically registered in the private DNS zone
Security Features
Azure DNS is built on Azure Resource Manager, which provides security across all resources in Azure DNS.
- Role-based access control
- Activity logs
- Resource locking
- Delete: Authorized users can still read and modify a resource, but they can't delete the resource
- Read-only: Authorized users can read a resource, but they can't delete or update the resource
Note
To delete a locked VM, users will need to contact a user with appropriate permissions - either an Owner or a User Access Administrator
Configure virtual network peering
- Regional VNet peering connects Azure virtual networks in the same region.
- Global VNet peering connects Azure virtual networks in different regions.
- Peering can be configured with VNets in the same subscription, across subscriptions, and across tenants.
- The virtual networks can't have overlapping IP addresses.
- After peering, VMs across diff VNets can communicate using private IPs.
Benefits of virtual network peering
- Private
- Network traffic between peered virtual networks is private.
- Traffic between the virtual networks is kept on the Microsoft backbone network.
- No public Internet, gateways, or encryption is required in the communication between the virtual networks.
- Performance
- A low-latency, high-bandwidth connection between resources in different virtual networks.
- Seamless
- The ability to transfer data across Azure subscriptions, deployment models, and across Azure regions.
- No disruption
- No downtime to resources in either virtual network when creating the peering, or after the peering is created.
Checking connectivity
- Initiated: When you create the peering to the second virtual network from the first virtual network, the peering status is Initiated.
- Connected: When you create the peering from the second virtual network to the first virtual network, its peering status is Connected.
Application workload connectivity options
- Create a virtual network subnet: As the VMs are part of the same virtual network, they can automatically perform name resolution and communite with the Azure AD DS domain controllers
- Configure virtual network peering: When you configure virtual network peering, you must also configure DNS settings to use name resolution back to the Azure AD DS domain controllers
Parameters to consider
- Allow forwarded traffic - Allows traffic not originating from within the peer virtual network into your virtual network
- Allow gateway transit - Allows the peer virtual network to use your virtual network gateway
- Use remote gateway - Only one virtual network can have this enabled
Configure VPN Gateway
A VPN gateway is a specific type of virtual network gateway that is used to send encrypted traffic between an Azure virtual network and an on-premises location over the public Internet.
- Site-to-site connections connect on-premises datacenters to Azure virtual networks
- Point-to-site (User VPN) connections connect individual devices to Azure virtual networks
- VNet-to-VNet connections connect Azure virtual networks (custom)
Note
Creating a virtual network gateway can take up to 45 minutes to complete.
VPN Gateway VS VNet Peering
- Vnet Peering
- Connect VNets from same or different regions (Global VNet peering)
- Allows for secure communication between VNets that are linked.
- Low Latency: Resources between diff VNets are connected using high bandwidth connections.
- Which is best for you?
- VNet Peering
- provides a low latency, high bandwidth connection useful in scenarios such as cross-region data replication and database failover scenarios.
- Since traffic is completely private and remains on the Microsoft backbone, customers with strict data policies prefer to use VNet Peering as public internet is not involved.
- Since there is no gateway in the path, there are no extra hops, ensuring low latency connections.
- VPN Gateways
- provide a limited bandwidth connection and is useful in scenarios where encryption is needed, but bandwidth restrictions are tolerable.
- In these scenarios, customers are also not as latency-sensitive.
- VNet Peering
Configure network routing and endpoints
UDR(user-defined route)s control network traffic by defining routes that specify the next hop of the traffic flow.
The hop can be a virtual network gateway, virtual network, internet, or virtual appliance.
System Route
- Routing: Process of finding/selecting a path for a traffic in one or across multiple networks
- Azure routing is setup by default
- Azure uses system routes to direct network traffic between virtual machines, on-premises networks, and the Internet.
- Information about the system routes is recorded in a route table.
- Routing tables are associated to subnets
- A route table contains a set of rules, called routes, that specifies how packets should be routed in a virtual network.
User-defined Network Routes
- Network Virtual appliance (NVA) – this is simply a specified optimized virtual machine for certain tasks.
- UDRs designed to override Azure default routing or add new routes
- Managed via Azure Route Table resource
- UDRs control network traffic by defining routes that specify the next hop (destination) of the traffic flow.
- The hop can be a virtual network gateway, virtual network, internet, or virtual appliance.
- Can be associated with more than one VNet subnets
Virtual Network service endpoints
A virtual network service endpoint provides the identity of your virtual network to the Azure service.
Endpoints allow you to secure your critical Azure service resources to only your virtual networks.
Benefits:
- Improved security for your Azure service resources
- Optimal routing for Azure service traffic from your virtual network
- Endpoints always take service traffic directly from your virtual network to the service on the Microsoft Azure backbone network
- Simple to set up with less management overhead
Available Services:
- Azure Storage
- Azure SQL Database and Azure SQL Data Warehouse
- Azure Database for PostgreSQL server and MySQL
- Azure Cosmos DB
- Azure Key Vault
- Azure Service Bus and Azure Event Hubs
private link
Azure Private Link provides private connectivity from a virtual network to Azure platform as a service (PaaS), customer-owned, or Microsoft partner services.
It simplifies the network architecture and secures the connection between endpoints in Azure by eliminating data exposure to the public internet.
Configure ExpressRoute and Virtual WAN
ExpressRoute
Use Azure ExpressRoute to create private connections between Azure datacenters and infrastructure on your premises or in a colocation environment.
ExpressRoute is best for handling enterprise-class and mission-critical workload
| Connection | Azure Services Supported | Bandwidths | Protocols | Typical Use Case |
|---|---|---|---|---|
| Virtual network, point-to-site | Azure IaaS services, Azure Virtual Machines | Based on the gateway SKU | Active/passive | Dev, test, and lab environments for cloud services and virtual machines. |
| Virtual network, site-to-site | Azure IaaS services, Azure Virtual Machines | Typically < 1 Gbps aggregate | Active/passive, Active/active | Dev, test, and lab environments. Small-scale production workloads and virtual machines. |
| ExpressRoute | Azure IaaS and PaaS services, Microsoft 365 services | 50 Mbps up to 100 Gbps | Active/active | Enterprise-class and mission-critical workloads. Big data solutions. |
ExpressRoute VS VPN Gateway
- ExpressRoute:
- Suitable for requirement for a high speeds, low-latency connection and high level of availability/resiliency.
- Suitable for mission critical workload.
- Access to all Azure services.
- Doesn’t suit smaller satellite offices that have a lower connectivity requirement.
- VPN Gateway:
- Suitable for prototyping, development, test, labs, and small production workloads.
- Suitable for the small organization.
- VPN isn’t designed to handle high data volumes.
Virtual WAN
- WAN stands for “wide area network”
- Azure Virtual WAN -> software-defined WAN sometimes called SD-WAN.
- Microsoft-managed, transitive, VNet hub-and-spoke architecture.
- Virtual WAN like an umbrella which includes lots of services:
- VNet peering
- All Azure VPN types - point-to-site, site-to-site, vnet-to-vnet VPN connections
- Azure ExpressRoute
- Azure Firewall
- Connectivity, security, monitoring and routing features like user-defined routing (UDRs), and route tables..
- With Virtual WAN you have a single management interface for these services.
Virtual WAN Global Transit
- Global transit network architecture will connect cloud and on-premises network endpoints across regions.
- Hubs are automatically interconnected via hub-to-hub links
- Using Azure Global Network's hub-to-hub connection, traffic from a cloud-connected branch in one region can reach another branch or VNet in a different region.
- Customers can transit traffic globally through the Microsoft Backbone without using AT&T, British Telecom, or others.
Configure Azure Load Balancer
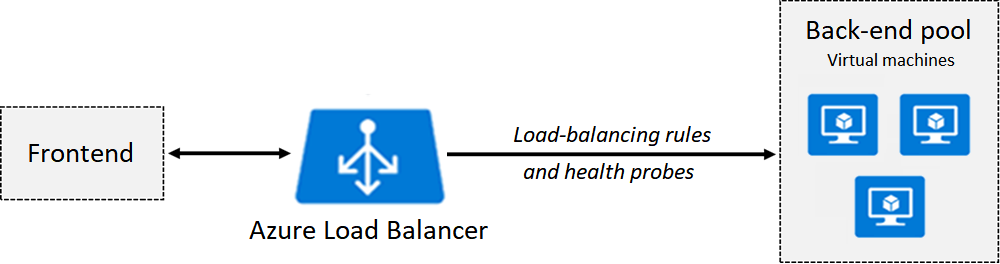
- Frontend configuration – IP address of your Azure Load Balancer. It's the point of contact for clients.
- Backend pool – Group of virtual machines that is serving incoming traffic.
- Adding or removing VMs from the backend pool reconfigures the load balancer without additional operations.
- Load-balancing rules determine how traffic is distributed to the backend pool.
- Health probes ensure the resources in the backend are healthy.
- Health probe dynamically adds or removes VMs from the load balancer rotation based on their response to health checks.
- When a probe fails to respond, the load balancer stops sending new connections to the unhealthy instances.
public load balancer
A public load balancer maps the public IP address and port number of incoming traffic to the private IP address and port number of the VM
internal load balancer
An internal load balancer directs traffic to resources that are inside a virtual network or that use a VPN to access Azure infrastructure
Internal load balancer types:
- Within a virtual network. Load balancing from VMs in the virtual network to a set of VMs that reside within the same virtual network.
- For a cross-premises virtual network. Load balancing from on-premises computers to a set of VMs that reside within the same virtual network.
- For multi-tier applications. Load balancing for internet-facing multi-tier applications where the backend tiers are not internet-facing. The backend tiers require traffic load-balancing from the internet-facing tier.
- For line-of-business applications. Load balancing for line-of-business applications that are hosted in Azure without additional load balancer hardware or software.
- This scenario includes on-premises servers that are in the set of computers whose traffic is load-balanced.
Note
A public load balancer could be placed in front of the internal load balancer to create a multi-tier application.
Configure session persistence
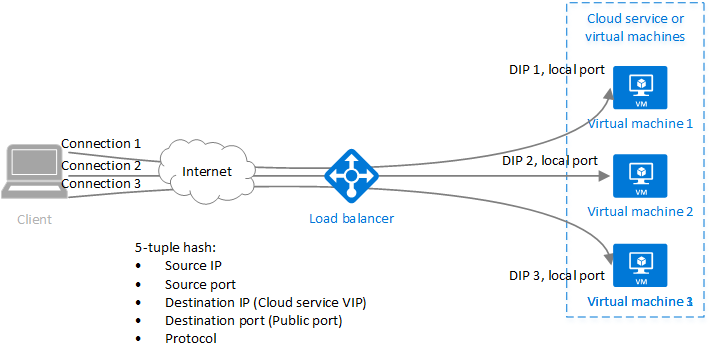
Session persistence specifies how traffic from a client should be handled.
The default behavior (None) is that successive requests from a client may be handled by any virtual machine. You can change this behavior.
- None (default) specifies any virtual machine can handle the request.
- Client IP specifies that successive requests from the same client IP address will be handled by the same virtual machine.
- Client IP and protocol specifies that successive requests from the same client IP address and protocol combination will be handled by the same virtual machine.
Create health probes
A health probe allows the load balancer to monitor the status of your app.
The health probe dynamically adds or removes VMs from the load balancer rotation based on their response to health checks.
When a probe fails to respond, the load balancer stops sending new connections to the unhealthy instances.
Configure Azure Application Gateway
Application Gateway manages the requests that client applications send to a web app.
Azure Application Gateway is a web traffic load balancer that enables you to manage traffic to your web applications.
- The Application Gateway uses application layer(OSI layer 7) routing.
- Application layer routing routes traffic to a pool of web servers based on the URL of a request.
- HTTP and HTTPS traffic only
- Traditional Load Balancer –> Layer 4 – TCP and UDP ( source/destination IP/port and protocol)
- Routing rules based on HTTP request parameters:
- URL path (web address)
- Host headers (request data)
- The back-end pool can include Azure virtual machines, Azure virtual machine scale sets, Azure App Service, and even on-premises servers.
Note
An Application Gateway uses the hostname, port and URL path to route requests to a web server
The Application Gateway distributes requests using round-robin
Features
- Round robin load balancing
- Cookie-based session affinity: Session stickiness ensures client requests in the same session are routed to the same back-end server.
- Session stickiness is critical for e-commerce apps, since you don't want a transaction disturbed by a load balancer.
- Web application firewall
- Checks each request for many common threats
- Based on the Open Web Application Security Project (OWASP)
- SQL-injection, Cross-site scripting, Command injection, HTTP request smuggling, HTTP response splitting, Remote file inclusion, Bots, crawlers, and scanners, and HTTP protocol violations and anomalies.
- Application Gateway routing
- Path-based routing
- Multiple-site routing
- Support Secure Socket Layer (SSL/TLS termination)
- Thus communication to backend servers is unencrypted.
- This functionality reduces web server encryption and decryption burden/costs.
- Redirection: Redirection can be used to another site, or from HTTP to HTTPS.
- Rewrite HTTP headers: Rewriting these HTTP headers helps you add security-related header fields or Removing response header fields that can reveal sensitive information.
- Custom error pages: Application Gateway allows you to create custom error pages instead of displaying default error pages. You can use your own branding and layout using a custom error page.
- Autoscaling: can scale up or down based on changing traffic load patterns. Autoscaling also removes the requirement to choose a deployment size or instance count during provisioning.
- Connection draining: Connection draining helps you achieve graceful removal of backend pool members during planned service updates.
- Once enabled, Application Gateway ensures all deregistering instances of a backend pool don't receive any new request while allowing existing requests to complete within a configured time limit.
- Support Websocket and HTTP/2 traffic: There's no user-configurable setting to selectively enable or disable WebSocket support.
- Zone redundancy: A Standard_v2 Application Gateway can extent multiple Availability Zones, offering better fault resiliency and removing the need to provision separate Application Gateways in each zone.
component set up
The Web Application Firewall is an optional component that handles incoming requests before they reach a listener.
The Web Application Firewall checks each request for many common threats, based on the Open Web Application Security Project.
Monitor and Back up Azure Resources
Configure file and folder backups
Azure backup benefits
Azure Backup is the Azure-based service you can use to back up (or protect) and restore your data in the Microsoft cloud.
Key benefits:
- Offload on-premises backups
- Back up Azure IaaS VMs
- Get unlimited data transfer
- Keep data secure
- Get app-consistent backups
- Retain short and long-term data
- Automatic storage management
- Multiple storage options
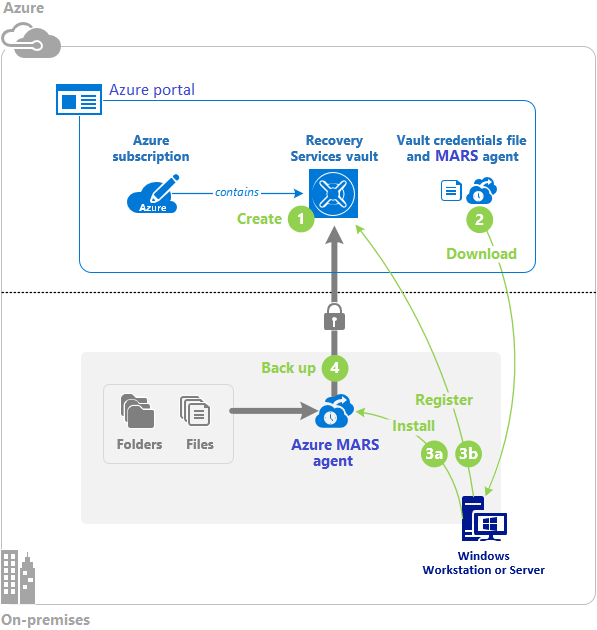
Configure virtual machine backups
- Snapshots: In development and test environments, snapshots provide a quick and simple option for backing up VMs that use Managed Disks
- Azure Backup: For backing up Azure VMs running production workloads
- Azure Site Recovery: protects your VMs from a major disaster scenario when a whole region experiences an outage due to major natural disaster or widespread service interruption
Azure Backup

Backup Methods
- Azure VM backup
- Azure Backup service directly backs up Azure virtual machines (VMs).
- Azure Backup adds a backup extension (VMSnapshot extension) to the Azure VM agent.
- This method backs up the entire VM. If you want to back up specific files and folders on the VM, install and use the MARS agent alongside the extension.
- MARS (Microsoft Azure Recovery Services)
- You can back up specific files and folders
- You can backup both Azure VM or on-premises Windows Server machines by running the MARS agent.
- DPM/MABS (Data Protection Manager/Azure Backup Server)
- On-premises machines can be backed up to DPM or Azure Backup Server (MABS). The backup server can be backed up to Azure Recovery Services.
- You can back up Azure VMs to the MABS that's running in Azure, and you can then back up the MABS to a Recovery Services vault.
Backup Report
- Help you get rich insights on your backups across your entire backup estate.
- Allocating and forecasting of cloud storage consumed.
- Auditing of backups and restores.
- Azure Backup leverages Azure Monitor logs and Azure workbooks for reporting.
- Supported for Azure VMs, SQL in Azure VMs, SAP HANA in Azure VMs, Microsoft Azure Recovery Services (MARS) agent, Microsoft Azure Backup Server (MABS), and System Center Data Protection Manager (DPM).
- Can be viewed across all backup items, vaults, subscriptions, and regions as long as their data is being sent to a Log Analytics workspace that the user has access to.
Azure Site Recovery
- Ensure business continuity and disaster recovery (BCDR)
- Site Recovery replicates workloads running on physical and virtual machines (VMs) from a primary site to a secondary location.
- When an outage occurs at your primary site, you fail over to a secondary location, and access apps from there.
- After the primary location is running again, you can fail back to it.
- Helps ensure business continuity by keeping business apps and workloads running during outages.
- You can replicate:
- Azure VMs from a primary region to a secondary region.
- VMware VMs to Azure
- On-premises VMs and physical servers to Azure, or to a secondary on-premises datacenter.
- Replication frequency as low as 30 seconds for Hyper-V
- Planned failovers for expected outages with zero-data loss.
- Unplanned failovers with minimal data loss, depending on replication frequency
Recovery Services Vault
Recovery Services vault is a storage entity in Azure that houses data.
The data is typically copies of data, or configuration information for virtual machines (VMs), workloads, servers, or workstations.
Configure Azure Monitor
Monitoring options
- Security Center: Manages the security of your infrastucture from a centralized location
- Application Insights: Monitors the availability, performance, and usage of your web applications whether they're hosted in the cloud or on-premises
- Azure Monitor: Collects, combines, and analyzes data from different sources
Note
All monitoring solutions require a Log Analytics workspace to store data collected by the solution and to host its log searches and views
Azure Monitor key capabilities
- Monitor and visualize metrics.
- Metrics are numerical values available from Azure resources helping you understand the health, operation and performance of your system.
- Query and analyze logs.
- Logs are activity logs, diagnostic logs, and telemetry from monitoring solutions; analytics queries help with troubleshooting and visualizations.
- Setup alerts and actions.
- Alerts notify you of critical conditions and potentially take automated corrective actions based on triggers from metrics or logs.
Azure Monitor components
Metrics
- Collect numeric data at regular intervals into time-series database.
- lightweight and capable of supporting near-real-time scenarios.
- What you can do with them?
- Analyze them interactively by using Metrics Explorer.
- Be proactively notified with an alert when a value crosses a threshold.
- Visualize them in a workbook or dashboard.
- Azure resources Overview page displays Azure Monitor data for many resources.
- Metrics can be accessed from the Azure Portal, the Monitor REST and.Net APIs, and analysis tools like Log Analytics and Event Hubs.
Logs
- Resource Logs
- Layer: Azure Resources
- Provide insight into operations that were performed within an Azure resource (the data plane).
- Examples: for SQL Server: Error, Timeout, Deadlock.
- The content of resource logs varies by the Azure service and resource type.
- Activity Log
- Layer: Azure Subscription
- Provides insight into the operations on each Azure resource in the subscription from the outside (the management plane)
- Also included Service Health events
- Use the Activity log to determine the what, who, and when for any write operations
- Azure Activity Directory Logs:
- Contain the history of sign-in activity and audit trail of changes made in Azure AD for a particular tenant.
Resource Logs
- Provide insight into operations that were performed within an Azure resource (the data plane).
- Azure resources generate logs automatically, but NOT collected without a diagnostic setting.
- Without storing logs, you cannot even view them.
- Diagnostic setting destinations
- Log Analytics workspace: Like a Datawarehouse, data repository, for more complex querying and alerting.
- Azure Event Hubs: Optimized for telemetry data, great when you are building event pipelines, forward outside of Azure
- Azure Storage: cheaper, long term retention, archival store, compliance purpose.
- Partner solution: Specialized integrations between Azure Monitor and other non-Microsoft monitoring platforms.
- Resource, Event Hub, and Azure Storage must be in the same region.
- Log content varies by Azure service and resource type.
- Resource log tables vary by collection type.
- Azure diagnostics: All data is written to the AzureDiagnostics table.
- Resource-specific: Data is written to individual tables for each category of the resource.
- All Azure services will eventually migrate to the resource-specific mode.
- Resource logs were previously referred to as diagnostic logs.
Activity Log
- Provides insight into subscription-level events.
- Includes information like when a resource is modified or property change at the service level
- Example: Virtual machine is started/stopped or Size changed or tier changed
- Activity Log events are stored for 90 days. To store this data for longer periods, export it to Storage Account, Log Analytics or Event Hubs.
- Activity logs you send to a Log Analytics workspace are stored in a table called AzureActivity.
Configure Azure alerts
Azure Monitor Alerts benefits
- Better notification system
- A unified authoring experience
- View Log Analytics alerts in Azure portal
- Seperation of Fired Alerts and Alert Rules
- Better workflow
Alert states
- New: The issue has been detected and has not yet been reviewed
- Acknowledged: An administrator has reviewed the alert and started working on it
- Closed: The issue has been resolved. After an alert has been closed, you can reopen it by changing it to another state.
Note
Alert state is set by the user. Monitor condition is set by the system.
Alert Types
There are four types of alerts:
- Metric alerts
- evaluates conditions on the resource metrics at regular intervals
- NOT Free, charged based on the number of time-series that are monitored.
- Log alerts
- monitors a resource by using a Log Analytics query
- NOT Free
- Activity log alerts
- monitors a resource by checking the activity logs
- FREE
- Smart detection alerts
- Smart Detection monitors the data received from your app, and in particular the failure rates.
- It uses machine learning algorithms to predict the normal failure rate.
- App Insights alerts you in near real time if your web app experiences an abnormal rise in the rate of failed requests.
Alert Rules
The key attributes of an alert rule are:
- Target Resource
- Defines the scope and signals available for alerting.
- A target can be any Azure resource.
- Example targets: a virtual machine, a storage account, a virtual machine scale set, a Log Analytics workspace, or an Application Insights resource.
- For certain resources (like Virtual Machines), you can specify multiple resources as the target of the alert rule.
- Signal
- Signals are emitted by the target resource and can be of several types. Metric, Activity log, Application Insights, and Log.
- Criteria
- Criteria is a combination of Signal and Logic applied on a Target resource.
- Examples: * Percentage CPU > 70%; Server Response Time > 4 ms; and Result count of a log query > 100.
- Alert Name
- A specific name for the alert rule configured by the user.
- Alert Description
- A description for the alert rule configured by the user.
- Severity
- The severity of the alert once the criteria specified in the alert rule is met.
- Severity can range from 0 to 4.
- Action
- A specific action taken when the alert is fired.
action groups
An action group is a collection of notification preferences defined by the owner of an Azure subscription.
An Action Group notifies a group of administrators when there is an issue.
- Notifications configure the method in which users will be notified when the action group triggers.
- Email Azure Resource Manager role – Send email to the members of the subscription's role.
- Email will only be sent to Azure AD user members of the role.
- Email will not be sent to Azure AD groups or service principals.
- Email/SMS message/Push/Voice - Specify any email, SMS, push, or voice actions.
- The maximum number of alerts supported through action group configuration settings is up to 100 notifications per hour
- Both Voice and SMS notifications are limited to no more than one notification every 5 minumtes
- Email Azure Resource Manager role – Send email to the members of the subscription's role.
- Actions configure the method in which actions are performed when the action group triggers.
- Automation runbook - An automation runbook is the ability to define, build, orchestrate, manage, and report on workflows that support system and network operational processes.
- A runbook workflow can potentially interact with all types of infrastructure elements, such as applications, databases, and hardware.
- Azure Function – Azure functions is a serverless compute service that lets you run event-triggered code without having to explicitly provision or manage infrastructure.
- ITSM – Connect Azure and a supported IT Service Management (ITSM) product/service. This requires an ITSM Connection.
- Logic App – Logic apps connect your business-critical apps and services by automating your workflows.
- Webhook – A webhook is a HTTPS or HTTP endpoint that allows external applications to communicate with your system.
- Automation runbook - An automation runbook is the ability to define, build, orchestrate, manage, and report on workflows that support system and network operational processes.
Azure Application Insight
- Provides application performance management (APM) and monitoring for live web apps.
- Azure Monitor vs Application Insight
- Azure Monitor metrics, alerts and logs - > Azure Infrastructure (performance and troubleshooting and optimization)
- Application Insights -> Business Application performance
- Developers and DevOps professionals can use Application Insights to:
- Automatically detect performance anomalies.
- Help diagnose issues by using powerful analytics tools.
- See what users actually do with apps.
- Help continuously improve app performance and usability.
- Application Insights:
- Supports a wide variety of platforms, including .NET, Node.js, Java, and Python.
- Works for apps hosted on-premises, hybrid, or on any public cloud.
- Integrates with DevOps processes.
- Has connection points to many development tools.
- Can monitor and analyze telemetry from mobile apps by integrating with Visual Studio App Center.
Monitor Targets
- Request rates, response times, and failure rates - Find out which pages are most popular, at what times of day, and where your users are. See which pages perform best.
- If your response times and failure rates go high when there are more requests, then perhaps you have a resourcing problem.
- Dependency rates, response times, and failure rates - Find out whether external services are slowing you down.
- Exceptions - Analyze the aggregated statistics, or pick specific instances and drill into the stack trace and related requests. Both server and browser exceptions are reported.
- Page views and load performance - reported by your users' browsers.
- AJAX calls from web pages - rates, response times, and failure rates.
- User and session counts.
- Performance counters from your Windows or Linux server machines, such as CPU, memory, and network usage.
- Host diagnostics from Docker or Azure.
- Diagnostic trace logs from your app - so that you can correlate trace events with requests.
- Custom events and metrics that you write yourself in the client or server code, to track business events such as items sold or games won.
Configure Log Analytics
Log Analytics is a service in that helps you collect and analyze data generated by resources in your cloud and on-premises environments.
- A separate Azure resource which act like a container for logs.
- Helps you collect and analyze data generated by resources in your cloud and on-premises environments.
- Logs are handled not meaningless strings of text, but instead organized in well defined schemas, helps analyze the data properly and efficiently.
- Workspace can handle terabytes of data per day.
- Log Management: example RBAC, retention, policies and more
- Log Exploration: including non-azure resources (example on-premises vm)
Configure Network Watcher
Network Watcher provides tools to monitor, diagnose, view metrics, and enable or disable logs for resources in an Azure virtual network.
Network Watcher is a regional service that enables you to monitor and diagnose conditions at a network scenario level.
- Set of monitoring tools.
- Focused on troubleshooting Azure Virtual Network issues
- Designed for network health of IaaS products which includes Virtual Machines, Virtual Networks, Application Gateways, Load balancers, etc.
- Not work for PaaS monitoring or Web analytics.
- Three major sets of capabilities
- Monitoring
- Diagnostics
- Metrics & Logging
- Monitor, diagnose and solve issues related to performance, connectivity, security, etc
- VNet traffic filtering problems
- Network routing problems
- Hybrid cloud connectivity issues related to Gateway or Express Route
- Every region has a unique Network Watcher instance.
- The hidden NetworkWatcherRG resource group contains Network Watcher resources.
Overview of Network Watcher
IP flowverify diagnose connectivity issuesNext hopdetermines if the traffic is being correctly routedVPN troubleshoottroubleshoots gateways and connectionsNSG flow logsmaps IP traffic through a Network Security GroupConnection troubleshootshows connectivity between source VM and destinationTopologygenerates a virtual diagram of resources
IP Flow
- IP Flow Verify Purpose: Checks if a packet is allowed or denied to or from a virtual machine.
- For example, confirming if a security rule is blocking ingress or egress traffic to or from a virtual machine.
- Based on 5-tuple - specify a source and destination IPv4 address, port, protocol (TCP or UDP), and traffic direction (inbound or outbound).
- IP flow verify tests the communication and reports success or failure.
- IP flow verify tells you which security rule allowed or denied the communication if the connection fails.
Network Watcher Tools
- Monitoring
- Topology view shows you the resources in your virtual network and the relationships between them.
- Connection Monitor allows you to monitor connectivity and latency between a VM and another network resource.
- Network performance monitor allows you to monitor connectivity and latencies across hybrid network architectures, Expressroute circuits, and service/application endpoints.
- Diagnostics
- IP Flow Verify allows you to detect traffic filtering issues at a VM level.
- Next Hop helps you verify traffic routes and detect routing issues.
- Connection Troubleshoot enables a one-time connectivity and latency check between a VM and another network resource.
- Packet Capture enables you to capture all traffic on a VM in your virtual network.
- VPN Troubleshoot runs multiple diagnostics checks on your VPN gateways and connections to help debug issues.
- Logging
- NSG Flow Logs allows you to log all traffic in your Network Security Groups (NSGs)
- Traffic Analytics processes your NSG Flow Log data enabling you to visualize, query, analyze, and understand your network traffic.